Build Your Audio Fortress
Managing Audio-Over-IP System Security.
There have always been security concerns with audio in commercial applications. Back when tape was the go-to medium, for example, keeping a close eye on who had access to the storage facility was important to stop people tampering with, or stealing, a record company's masters. Similar media-management concerns are real in the digital domain. In fact, threats of data theft are multiplied due to the ability to share Gigabytes with the world in seconds. So despite the significant practical benefits of modern audio-over-IP systems, there are completely new security concerns to consider, and best practices to adopt.
This article will help to identify the potential security shortcomings — whether accidental or malicious — of your audio-over-IP system, and suggest ways to limit your system's exposure to user slip-ups and bad actors alike.
Step One: Simple Common Sense
Despite the advanced technological nature of a networked audio system, the first step in maintaining secure and stable operation is a human one, according to Will Hoult, Focusrite's Product Manager for Commercial and Professional Audio. “Access to any audio system should be managed using a common-sense approach. In an analogue studio scenario, the connections between rooms and devices are made using physical patch cables. If I was operating in control room #1 and saw that the live room was patched to control room #2, I would first check to see if someone else was using them before pulling the patch cables out of the panel. Only when I was sure that I could re-patch audio without affecting others' workflows would I start unplugging cables. This kind of process should also happen in a digital system, where all operators accessing the system follow the same procedure." Assuming everyone abides by the rules, the vast majority of audio interruptions can be avoided. But that's easier said than done, especially when you have a large facility and lots of operators accessing the audio network at the same time.
Audio-over-IP systems have the huge advantage of multi-user interoperability, but with that comes several potential security pitfalls. Steps can be taken to control who can access mission-critical audio data.
Controlling Users & Permissions
One of the main benefits of a networked audio system is that it allows multiple users to easily access the same audio, and process it independently of others. So it's not hard to imagine a situation where in-use audio is mistakenly re-routed or accidentally remotely controlled.
There are several failsafes built into Dante — the protocol on which RedNet operates — that allow the user to limit access to mission-critical functions, as Will Hoult explains. “With Dante Firmware v3.10 and Dante Controller v3.10 and later, Audinate has implemented a PIN lock feature, where a four-digit code needs to be entered before changes can be made. Lockable functions include routing settings, sample-rate changes, remote controlled reboot of devices, and network settings changes. All these are crucial for uninterrupted audio."
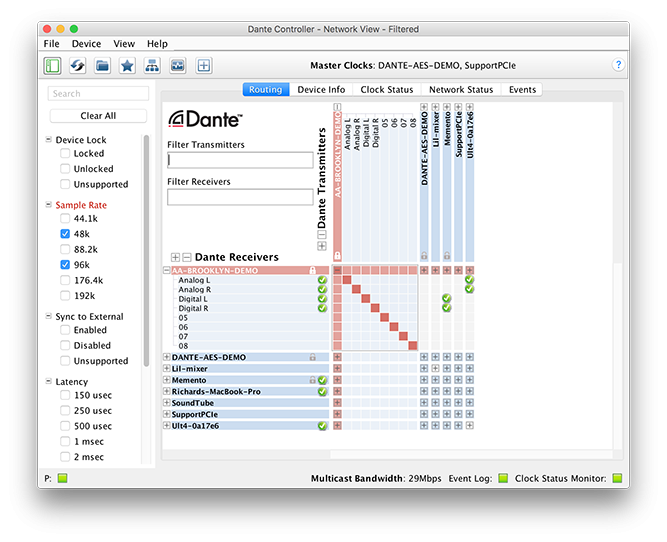
The lock feature in Dante Controller v3.10. A four-digit PIN is required to change the settings of locked devices.
The lock function itself is not immune to disruption though. For example, if one user has finished their session with their routing setup locked, the proceeding user will see locked units that are not being used. It's here where human intervention and pre-agreed system-access procedures are important, especially on a network spread over a wide geographic area. (On a fibre-optic network, Dante-connected devices can operate kilometers apart.)
“The best practice in this case," says Hoult, “is to assume that, if a routing is locked, it's in use. If you suspect someone forgot to unlock it, then you follow a simple communication procedure — maybe a phone call or text message — before making changes."
Wall-In Your Audio Network
Locking Dante's routing functions is one way to avoid accidental mis-clicks by authorised network users. But you may want to keep entire sections of your network off-limits, to prevent people with malicious intent accessing your audio. This is especially appropriate in applications where the audio content is sensitive — think confidential commercial and governmental applications, and high-profile music and film projects. The key here is keeping the data out of reach, while maintaining the flexibility of the multi-user system.
“You wouldn't install an Ethernet port in the reception area of your high-security data storage centre…" — Will Hoult, Focusrite
The first, most obvious, step is to keep bad actors away from network ports. “The most basic thing is to restrict physical access to your network," says Hoult. “You wouldn't install an Ethernet port in the reception area of your high-security data storage center, for example. So the first step is not to allow easy physical access to your network."
This might be easier said than done, especially in places with lots of people 'supposed' to be there, such as a film set. “You might have a legitimate reason to be in a room, but not to be on the network. So the next thing we can do after limiting the number of physical ports is to control who gains access to the network itself. We can implement username and passwords to grant permission to a controlled list of users. We can also ring-fence the audio equipment on a Virtual Network, and control permissions using an Access Control List (ACL). That's a very simple networking implementation; it's part of Internet Protocol (IP), so an IT department would be capable of setting that up."

Network security becomes especially important in scenarios where audio devices are spread over a large and unguarded physical area.
Another access-control option — which is suitable when you have a known list of equipment — is to control which devices appear on the network. Whether it's a computer, a standalone recorder, or an A-D/D-A interface, every networked device has a unique identifier called a MAC address. Access can be granted only to approved devices. “Setting this up will have to be done in collaboration with the IT administrator," says Hoult. “But hopefully they will already know far more about this than you do as an audio engineer!"
Streamlining Network Traffic
Another potential source of disruption is from other traffic on the same network as your audio. Hoult: “It's generally OK to run your audio alongside other network traffic, providing your IT team is willing and able to configure your network to prioritise small audio-related network packets. RedNet uses standard network processes such as Quality of Service (QoS), which basically puts a priority number on every packet of network traffic that passes through the switch. If the switch receives two packets at once, it will let through the packet with the higher priority first."
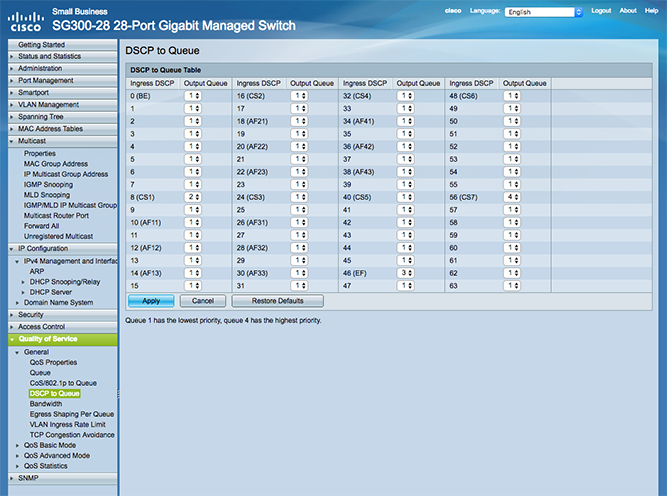
The QoS configuration window of a Cisco network switch.
On smaller systems, or in scenarios where there isn't dedicated IT support — such as a recording studio — the notion of setting up an IP network could be quite daunting. Will Hoult has some words of guidance for network newbies, specifically in choosing equipment that will let you configure the system to be beneficial to your audio traffic. “Make sure you buy 'Managed Layer-3' network switches; they're slightly more costly, but offer more flexibility when it comes to configuring and customising your network. For username and password control, you will need a server, which will give the added benefit of providing remote storage for things like session templates. A server is very simple to set up, and it's the kind of thing that you can implement with low-cost software or freeware, and a very affordable computer such as a Raspberry Pi. The actual cost of implementing it is very low."
By following these guidelines, instigating best practices and establishing an appropriate access procedure between users, you can be safe in the knowledge that your audio will be uninterrupted and in safe hands at all times. We admit that it's a lot more involved than putting a lock on the tape storage vault. But as Bob Dylan said in 1964, “the times they are a-changin'".

